Styra DAS Policy Lifecycle
The Policy Lifecycle is a standard set of tasks used to deploy policies in a production-ready software system.
The following figure shows the key stages of the Policy Lifecycle and the typical activities that take place in each stage.
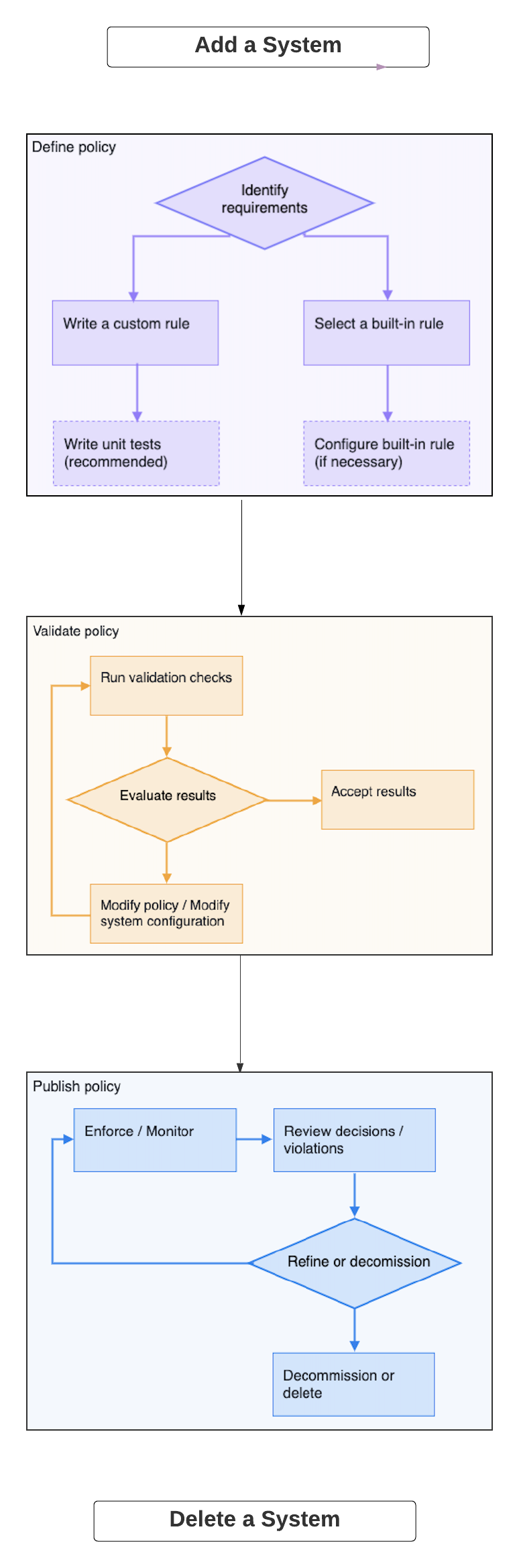 Policy Lifecycle
Policy LifecycleThe Policy Lifecycle involves the following tasks:
- Define Policy Rules using built-in or custom Rules.
- Validate and analyze Policies before distribution to analyze the Policy's impact if you were to enforce it.
- Publish Policies to monitor and enforce compliance.
- Replay enforcement decisions in real-time or in the historical context.
Define Policy Rules
To define Policies, choose from the predefined set of built-in Rules or write custom Rules. The predefined built-in Rules have parameters that can be modified to tailor the Rule to your specific needs. For example, using the Repository Safety Rule, you can specify the registries from which the images can be downloaded and determine which repositories are permitted for each registry. The built-in Rules provide a starting point and cover many of the most widely-accepted best practices for managing a real-world software system.
To add additional guardrails not specified by any of the pre-built Rules, you can write custom Rules using the Cloud Native Computing Foundation (CNCF) OPA policy language.
For additional information about OPA's Rego policy language, see the Open Policy Agent documentation and the description of Rego.
Validate and Analyze Policies
After a Policy is created, Styra DAS analyzes the Policy in different ways to understand the impact the Policy will have on your cluster. You can perform this analysis for both built-in and custom Rules using the Validate command in the Policy Editor.
The following tasks show how to validate and analyze Policies.
- Run the unit tests written for custom Policies, and report the test results.
- Perform an audit that identifies the resources in the cluster that violate a given Policy.
- Display a historical record of the decisions to predict what happens if you enforce a proposed Policy.
- Replay past decisions during validation enables you to see how a new Policy that has not yet been enforced would result in different decisions than those that were made in the past.
Publish Policies
Before publishing Policies, complete the following tasks:
- Adjust the Policy and/or the resource configuration to meet your requirements.
- Confirm the Policy meets your requirements.
- Review the Policy validation results.
Once the Policy is published, the Open Policy Agent handles enforcement by periodically downloading the latest policy and making decisions on creating, updating, and deleting operations sent to the API server.
If a policy is published with monitoring enabled, Styra periodically searches through all the resources on your cluster and finds a list of resources that violate the current policy.
Replay Enforcement Decisions
You can see all the Decisions OPA is enforcing in real-time. You can also drill down into Decisions for individual Systems and filter the results to see details for Systems that meet specific criteria.
Replaying Policy decisions is an instrumental stage in the Policy Lifecycle, especially when you want to verify compliance with auditors or industry regulators to investigate the security incidents.