Google GS Bucket Access
Styra DAS supports Google GS bucket systems. This document describes how to setup an GCP IAM Role, Service Account, and G3 buckets for secure DAS GS access. GS buckets can be utilized in bundle registry, decision log, and activity log exporters.
Using /v1/workspace/S3Config API
Google GS buckets are configured from the following data elements:
- Bucket URL. For example,
gs://styra-storage/folder. - Custom endpoint. For example,
https://storage.googleapis.com. - Region. For example,
us-east1orauto. - Access Key.
- Secret.
The Styra DAS UI hides the URL gs://, s3://, and azblob:// prefixes.
Verify Example, /v1/workspace/s3/verify-config:
curl --request POST \
--url ''$DAS_TENANT'/v1/workspace/s3/verify-config' \
--header 'authorization: Bearer '$DAS_WORKSPACE_TOKEN'' \
--header 'content-type: application/json' \
--data \
'{
"url": "gs://styra-storage/decisions",
"endpoint": "https://storage.googleapis.com"
"region": "auto",
"access_keys": "workspace/decision-streaming/decisions/s3",
}'
Secure Google GS bucket access
Use Google IAM Management Console
Perform the following steps to create new user, setup permissions, and collect the access keys.
The names styra, Styra Storage Object, StyraServiceAccount, and styra-storage are used as illustrations and can be changed to follow any enterprise naming conventions.
-
Create a new Google Custom Role from existing Storage Object Admin.
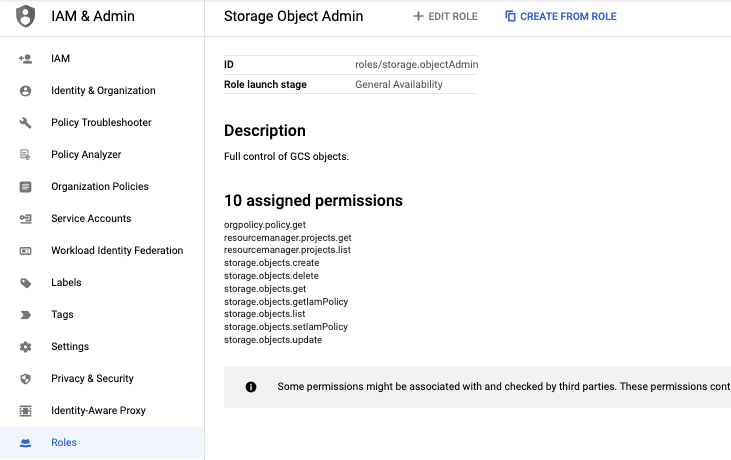 Figure 1 - Create a new Google Custom Role
Figure 1 - Create a new Google Custom Role
-
Create Role
Styra Storage Object.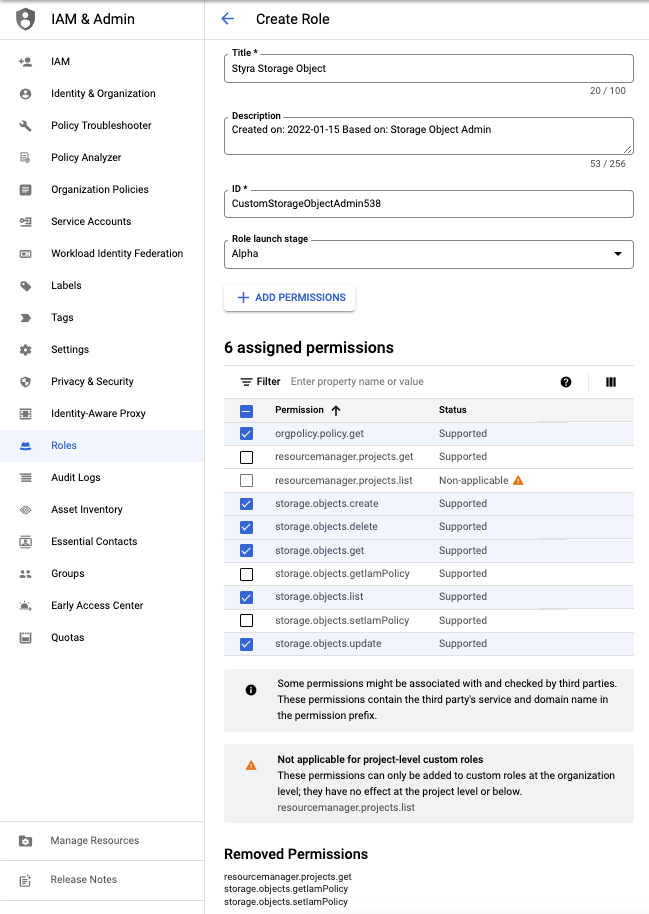 Figure 2 - Create Role
Figure 2 - Create Role
-
Set the created role name to
Styra Storage Object. -
Remove the following permissions:
- resourcemanager.project.get
- storage.object.getIamPolicy
- storage.object.setIamPolicy
-
Select only the following permissions:
- orgpolicy.policy.get
- storage.objects.create
- storage.objects.delete
- storage.objects.get
- storage.objects.list
- storage.objects.update
-
Click the Create button.
-
Use Google Storage Manager
Perform the following Google Cloud Platform actions:
Styra recommends you setup Service Account HMAC to control access to buckets.
-
Navigate to Cloud Storage >> Settings page.
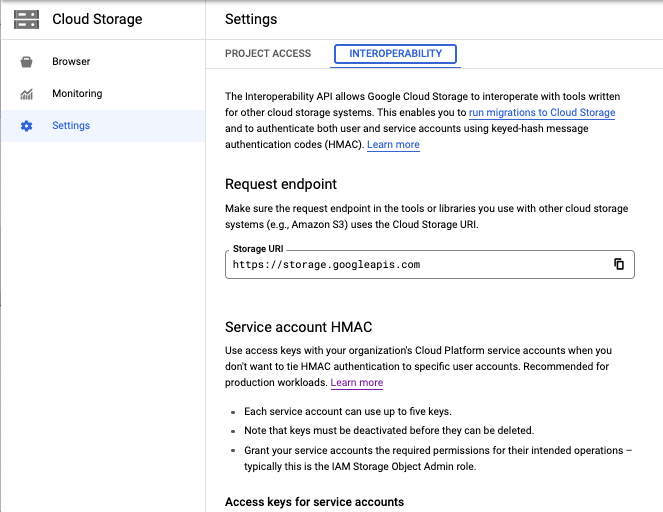 Figure 3 - Cloud Storage Settings
Figure 3 - Cloud Storage Settings
-
Select the Interoperability tab and then Create a key for another service account.
-
Select Create New Account.
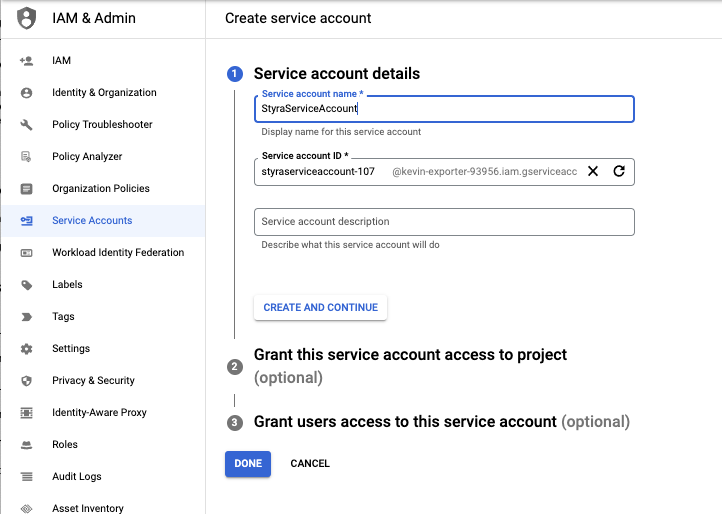 Figure 4 - Create a New Google Storage Service Account
Figure 4 - Create a New Google Storage Service Account
-
Set the name to
StyraServiceAccount. -
Click on the CREATE AND CONTINUE button.
-
Save the account Access key and Secret for later use when configuring DAS GS components.
-
-
Navigate to Cloud Storage >> Browser and select the CREATE BUCKET button.
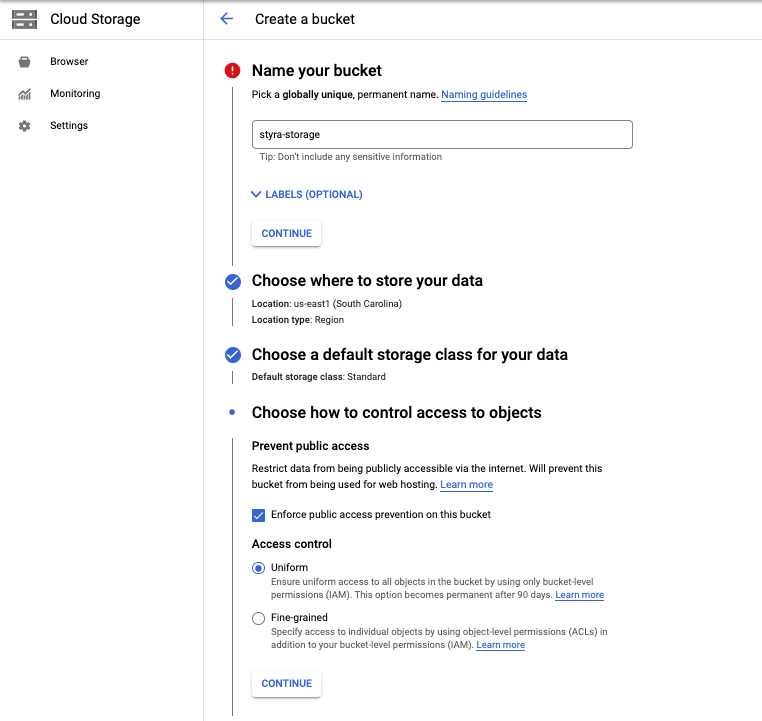 Figure 5 - Create a Google Storage Bucket
Figure 5 - Create a Google Storage Bucket
noteStyra recommends you to enable Enforce public access prevention on this bucket and set a lifecycle policy.