Styra DAS Terraform System Type Overview
Terraform is an open-source tool to describe, manage, and automate your infrastructure as code for most cloud providers. The Styra DAS Terraform system type enforces guardrails on cloud resources you manage with Terraform by evaluating the same policies against Terraform HCL code, Terraform plans, Terraform state, and cloud provider resources. For example, a team could require all AWS S3 buckets use at least AES-256 encryption to ensure your S3 data is always encrypted at rest to satisfy your organization's compliance and security requirements.
The Styra DAS Terraform system type supports Terraform v0.12 and higher.
Terraform Code Evaluation
Styra DAS Terraform systems support evaluation of policy on Terraform HCL code files (.tf and .tf.json files) using the Styra CLI validate check-local command. Using this Styra CLI command, policy guardrails can be applied to Terraform code during the development process, including local development, cloud git services, and CI/CD pipelines. When implemented in a pre-commit hook or in build processes, code scanning can be used to prevent Terraform code which results in policy violations from being committed/pushed to git or to stop CI/CD pipeline builds from continuing with non-compliant code.
See the Use the Styra DAS CLI for Terraform Policy doc for Styra CLI installation and configuration instructions for Terraform code scanning.
Terraform Plan Evaluation
Terraform plans generated both via Terraform Cloud or Terraform Enterprise and via the Terraform CLI in local development environments and in CI/CD can be evaluated by Styra DAS for policy violations. Build and deploy process can be configured to stop further execution if a Terraform plan is found to contain policy violations to prevent non-compliant resources from being deployed to cloud services.
Using Styra DAS with the Terraform CLI
Terraform can run locally and in CI/CD workflows by using the Terraform CLI to plan, apply, and manage cloud resource changes. Then use the Styra CLI to pass in the Terraform plan and evaluate it against policies defined in Styra DAS by your organization. The diagram below shows how the Styra CLI fits in with a typical Terraform plan and apply flow.
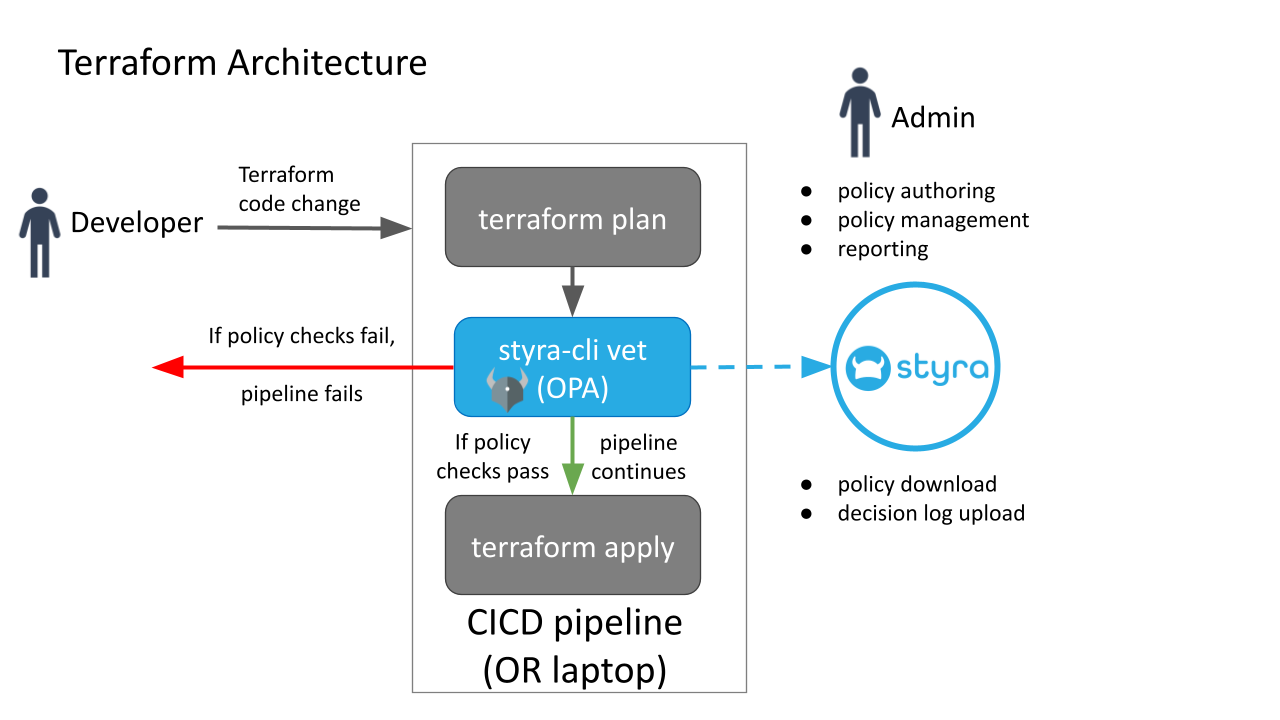 Figure 1 - Styra DAS Integration with Terraform
Figure 1 - Styra DAS Integration with TerraformSee the Use the Styra DAS CLI for Terraform Policy doc for Styra CLI installation and configuration instructions for Terraform plan scanning.
Using Styra DAS with Terraform Cloud or Terraform Enterprise
Terraform Cloud is HashiCorp's managed Terraform service offering which enables running Terraform across multiple cloud environment securely and at scale. Terraform Enterprise is the self-hosted edition of Terraform Cloud.
The Styra DAS Terraform system type supports a direct integration with Terraform Cloud/Enterprise using Terraform run tasks, a feature which allows integrating third-party tools in the post-plan/pre-apply stage of a Terraform Cloud/Enterprise run for workspaces using Terraform v0.12 or later. The diagram below shows the run task integration architecture for Terraform Cloud, including the post-plan invocation of Styra DAS policy evaluation with the Terraform plan and run details. The run task integration architecture for Terraform Enterprise is identical to the Terraform Cloud architecture.
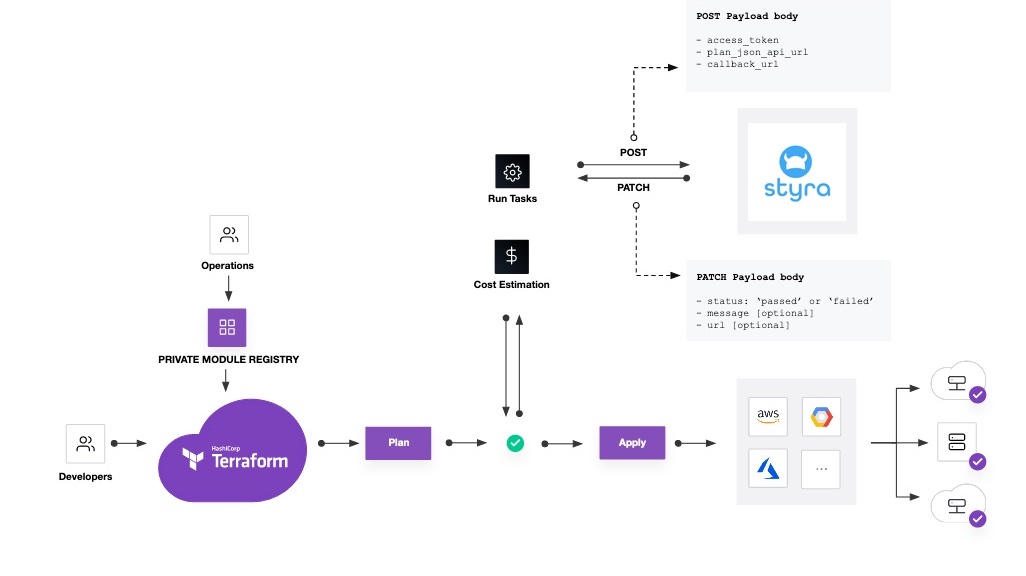 Figure 2 - Architecture of Styra DAS for Terraform Cloud
Figure 2 - Architecture of Styra DAS for Terraform CloudBy configuring the run task integration with Styra DAS, Terraform Cloud/Enterprise plans are always evaluated against your Styra DAS Terraform policies before the plan's changes can be applied to cloud resources. No infrastructure or agents need to be deployed—just connect your Styra DAS workspace with your Terraform Cloud/Enterprise organization and start enforcing infrastructure-as-code guardrails with Styra DAS.
Integration with Terraform Enterprise run tasks is only available on Styra DAS Enterprise.
See the Use Styra DAS with Terraform Cloud/Enterprise doc for instructions to integrate Styra DAS with Terraform Cloud and Terraform Enterprise run tasks.
Terraform State Compliance
To help teams meet organization or industry infrastructure compliance requirements, it is often necessary to continually monitor deployed infrastructure resources and identify resources which violate policy guardrails. Styra DAS Terraform systems support connecting Terraform state as a Styra DAS system data source for policy evaluation of deployed resources against the same policy guardrails used for code and plan scanning.
Terraform stores the configuration of resources deployed to cloud services in state data (e.g., the configuration of an AWS S3 bucket or a Google GKE cluster). Your chosen Terraform backend configuration determines how this state data is stored. Terraform state data stored in AWS S3, Google Cloud Storage (GCS), Terraform Cloud or Terraform Enterprise workspaces, git, or in an http-accessible datastore can be scanned by Styra DAS Terraform systems to determine the compliance status of deployed resources using the policy guardrails defined in those systems.
Violations in Terraform state are reported in the Styra DAS system Compliance tab where they can be reviewed for remediation actions. The number of Compliance violations is tracked over time in a Terraform system's Monitoring tab to show progress addressing violations with deployed resources. Styra DAS evaluates Compliance results automatically every hour using the last Terraform state version in a Terraform system, and users can additionally run an on-demand Compliance check using the "Scan for violations" button in a Terraform system's Compliance tab.
See the Styra DAS Terraform State Compliance doc for instructions to connect your Terraform state with Styra DAS for compliance monitoring.
Learning Topics
Learn more about how to use the Styra DAS Terraform system type.
-
System Setup:
- Styra CLI - Use Styra DAS with the Terraform CLI and Styra CLI.
- Terraform Cloud and Terraform Enterprise - Use Styra DAS with Terraform Cloud or Terraform Enterprise.
- Terraform State Compliance - Use Styra DAS with Terraform state.
- Styra DAS Terraform System Troubleshooting - Resolutions to Terraform system setup issues.
-
Terraform Policies:
- Terraform Policy Authoring - Use Styra's pre-built Terraform policy rules or author custom policies.
- Terraform Decision Masking - Mask sensitive values in the Terraform plan input before logging to the decision log.
- Terraform Policy Library Rules - Styra's pre-built library of Terraform policy rules for the AWS, Azure, Google Cloud, and Kubernetes Terraform providers.
See it in Action
If you prefer to see the Styra DAS Terraform system type in action, refer to our tutorials: