Policy Authoring
Envoy Policy authoring defines which HTTP APIs should be allowed into and out of a service running next to Envoy. Those policies are enforced by Envoy, and a rejected API request is never seen by the service. Additionally, you can write a policy that your service calls into explicitly to provide additional information that Envoy does not have. It is your service's responsibility to enforce that decision appropriately.
Pre-installed Policies
When you add the Envoy system, several policies are automatically installed. In the Styra DAS, click app, egress or ingress folders from your Envoy system to see the policies.
-
app: Custom policy that you can use if your application needs additional policy decisions from OPA.
-
egress: Policy that either allows or denies outgoing traffic.
-
ingress: Policy that either allows or denies incoming traffic.
Write Ingress and Egress Policies
When authoring policies, use Rego, Open Policy Agent's policy language.
For an introduction to Rego, Styra recommends you review the following materials:
-
OPA Documentation Introduction to OPA or Rego Documentation
-
Free Video Training: Styra Academy
When writing Rego policies, you need to know the format of the JSON that is provided to each of your policies as input. The following shows a sample input provided by Envoy for Ingress and Egress policies. This sample includes source, destination, the request itself, and additional metadata.
{
"attributes": {
"destination": {
"address": {
"socketAddress": {
"portValue": 8000,
"address": "10.25.95.68"
}
}
},
"metadataContext": {
"filterMetadata": {
"envoy.filters.http.header_to_metadata": {
"policy_type": "ingress"
}
}
},
"request": {
"http": {
"headers": {
":authority": "example.com",
":method": "GET",
":path": "/foo?query=bar",
"accept": "*/*",
"authorization": "Basic Z2ghmcxpZTpwYANzezBwZD==",
"content-length": "0",
"user-agent": "curl/7.74.0-DEV",
"x-ext-auth-allow": "yes",
"x-forwarded-proto": "http",
"x-request-id": "7b18247b-e2fd-4002-a8e2-ff2a9b7ceca0"
},
"host": "example.com",
"id": "5026273330918463281",
"method": "GET",
"path": "/foo?query=bar",
"protocol": "HTTP/1.1"
},
"time": "2021-09-13T16:55:30.872223Z"
},
"source": {
"address": {
"socketAddress": {
"portValue": 33772,
"address": "10.25.95.69"
}
}
}
},
"parsed_body": {},
"parsed_path": [
"foo"
],
"parsed_query": {
"query": ["bar"]
},
"truncated_body": false,
"version": {
"encoding": "protojson",
"ext_authz": "v3"
}
}
When writing policies, the allow or deny rules are written to describe the conditions under which a request is allowed or denied. By default, requests are all allowed, so you must write policy to deny them.
For example, if you want to allow all GET requests and deny all POST requests to the root path, then write the following allow and deny rule.
# allow GET requests to the root path
allow {
input.attributes.request.http.method == "GET"
input.attributes.request.http.path == "/"
}
# deny POST requests to the root path
deny {
input.attributes.request.http.method == "POST"
input.attributes.request.http.path == "/"
}
Response Options
Styra DAS automatically creates response options for the following:
Allow Decisions
As covered in writing egress/ingress policies, Styra DAS returns allow decisions based on the allow/deny rules written.
Headers Decisions
You can optionally write rules that return additional, custom headers that Envoy will add to the request before forwarding to the microservice. To implement this action, you will write rules that define headers to be a JSON object that maps the headers name to its value.
For example, if you want to add the headers X-Via-Proxy: Envoy and X-Via-OPA: true then write the following headers rules.
headers["X-Via-Proxy"] = "Envoy"
headers["X-Via-OPA"] = true
The example above has empty rule bodies so the headers are included on every request. If required, you could add conditions to the rule bodies.
status_code Decisions
You can optionally write rules that control the HTTP status code. By default, the status_code will be 200 if allow is true and 403 if deny is true. But, if you want to override that behavior, you can define the status_code variable to any desired value.
For example, if you want to return 200 when allow is true and 400 when deny is true then write following status_code rules.
status_code = 200 { allow }
status_code = 400 { deny }
Write App rules for OPA-aware Applications
In addition to the Ingress and Egress policies, the Envoy systems also support application policies. The structure of these policies are customizable according to the application's requirements. By default, the module policy.app contains allow and deny - rules similar to Ingress and Egress policies, but you can remove those and write any Rego that you want.
An application can directly query the OPA embedded in data plane sidecar, usually listening at localhost:8181, for application-specific authorization decisions. The default data document for application policies is data.application.main. This exercises the allow or deny rule created in policy.app module.
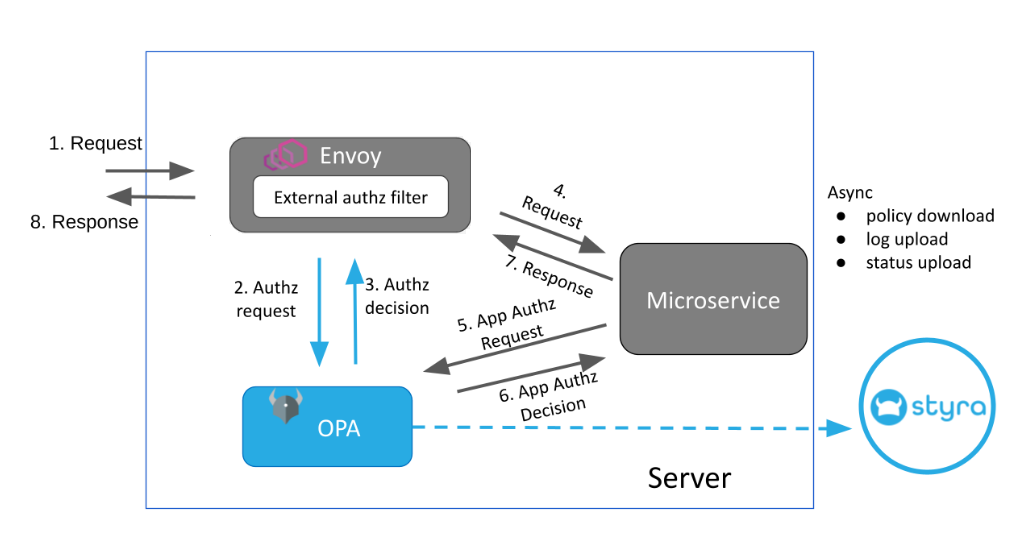 Figure 1 - Envoy Architecture for OPA-aware Applications
Figure 1 - Envoy Architecture for OPA-aware ApplicationsTo query the App-specific main rule:
curl -XPOST localhost:8181/v1/data/application/main \
-d '{
"input": {
"method": "GET",
"path": [
"finance",
"salary",
"bob"
],
"user": "bob"
}
}'
{
"decision_id":"d9abc874-d27b-4ee4-9542-c044871484c9",
"result": {
"allowed": true,
"code": 200,
"status_code": 200,
"outcome": {
"allowed": true,
"code": 200,
"status_code": 200,
"policy_type": "app",
"system_type": "envoy"
}
}
}
The decision mappings for Envoy systems rely on the presence of well-known fields to correctly parse the results. The decision mapper expects an outcome structure in the result with two required fields:
allowedpolicy_type
{
"outcome": {
"allowed": false, // boolean value to determine if decision was Allowed or Denied
// an absence of this value will mark the decision as Unknown
"policy_type": "app" // classifies the decision as an app decision
// useful for filtering decisions by type in the Decisions UI
}
}
The allow rule for policy.app can also be queried directly at the path http://localhost:8181/v1/data/policy/app/allow, but since the returned result will not contain the outcome object, the decisions will mark it as Unknown in the DAS UI. Querying the rule through the main rule at policy.application.main ensures that the returned decision document is well-formed and conforms to the requirements of the decision mapper.