Amazon S3 Bucket Access
Styra DAS requires configuration of an AWS User and an Amazon S3 bucket in order for Styra DAS to securely access Amazon S3. Styra DAS supports Amazon S3 and S3 compatible bucket systems. Amazon S3 buckets can be utilized in Amazon S3 data sources, bundle registry, decision log, and activity log exporters.
Using /v1/workspace/S3Config API
The S3 buckets are configured from the following data elements:
- Bucket URL. For example:
s3://styra-storageors3://styra-storage/folder - Custom endpoint or S3 compatible system endpoint. For example:
https://s3.amazonaws.com. - Region. For example:
us-east-1. - Access key ID
- Secret access key
The Styra DAS UI hides the URL gs://, s3://, and azblob:// prefixes.
Verify Example, /v1/workspace/s3/verify-config:
curl --request POST \
--url ''$DAS_TENANT'/v1/workspace/s3/verify-config' \
--header 'authorization: Bearer '$DAS_WORKSPACE_TOKEN'' \
--header 'content-type: application/json' \
--data \
'{
"url": "s3://styra-storage/decisions",
"endpoint": ""
"region": "us-east-1",
"access_keys": "workspace/decision-streaming/decisions/s3",
}'
Secure AWS S3 bucket access
Secure Amazon S3 bucket access through the AWS IAM Management Console or the Amazon S3 Manager.
Use AWS IAM Management Console
Perform the following steps to create new user, setup permissions, and collect the access keys.
The names styra, StyraAccess, and styra-storage are used as illustrations and can be changed to follow any enterprise naming conventions.
-
Create a new AWS user
styraand select Access key - Programmatic access.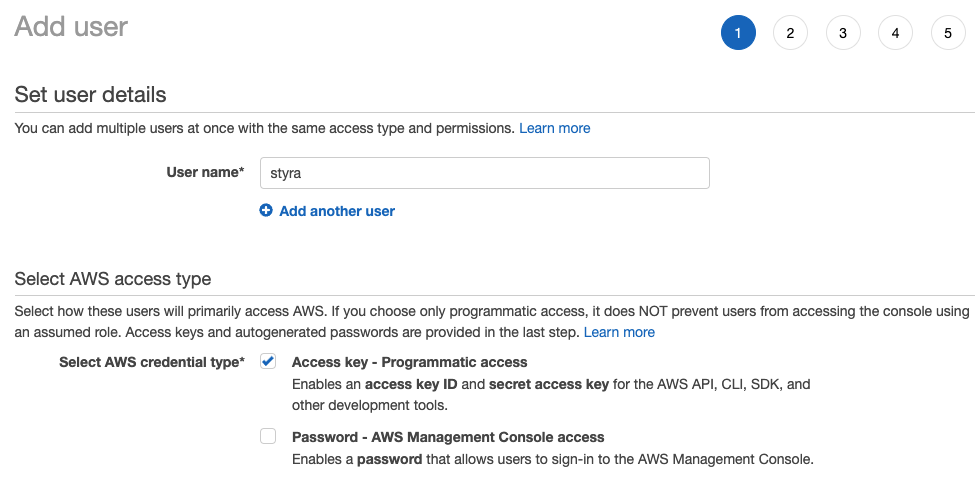 Figure 1 - IAM User
Figure 1 - IAM User
-
Create a
StyraAccesspermissions policy and select Create policy to start the new permissions policy editor.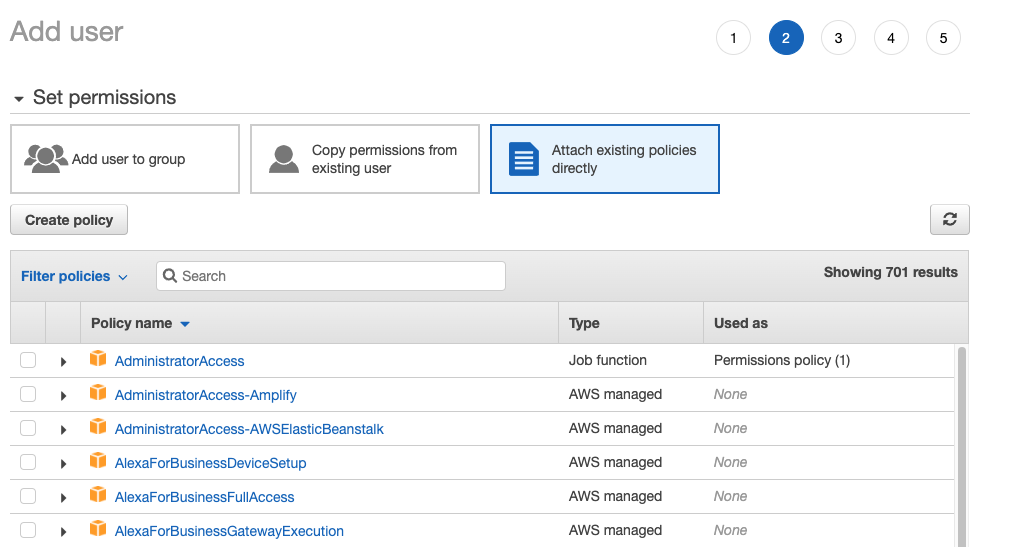 Figure 2 - IAM Policy
Figure 2 - IAM Policy
-
Setup permissions policy secure access
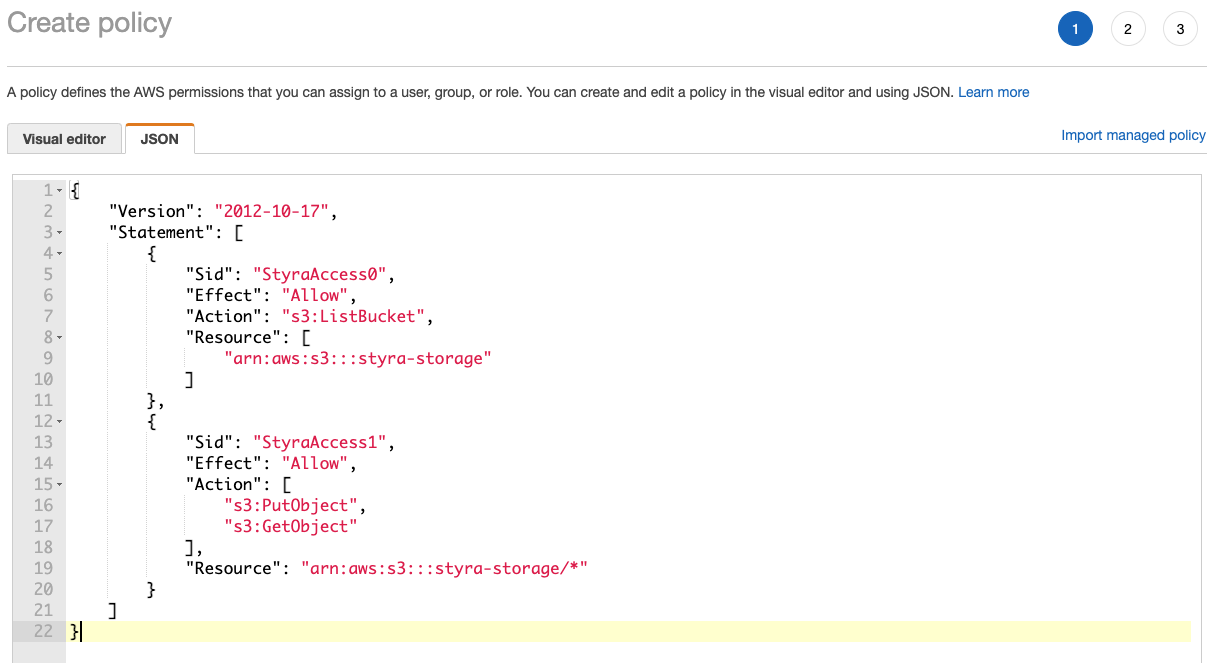 Figure 3 - IAM Create Policy
Figure 3 - IAM Create Policy
Add a policy for each S3 bucket or S3 bucket folder to grant DAS access to. To constrain access to a specific folder, change the resource to
arn:aws:s3:::styra-storage/foldername/*.Sample Permissions Policy{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "StyraAccess0",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": [
"arn:aws:s3:::styra-storage"
]
},
{
"Sid": "StyraAccess1",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject"
],
"Resource": "arn:aws:s3:::styra-storage/*"
}
]
} -
Save the
StyraAccesspermissions policy.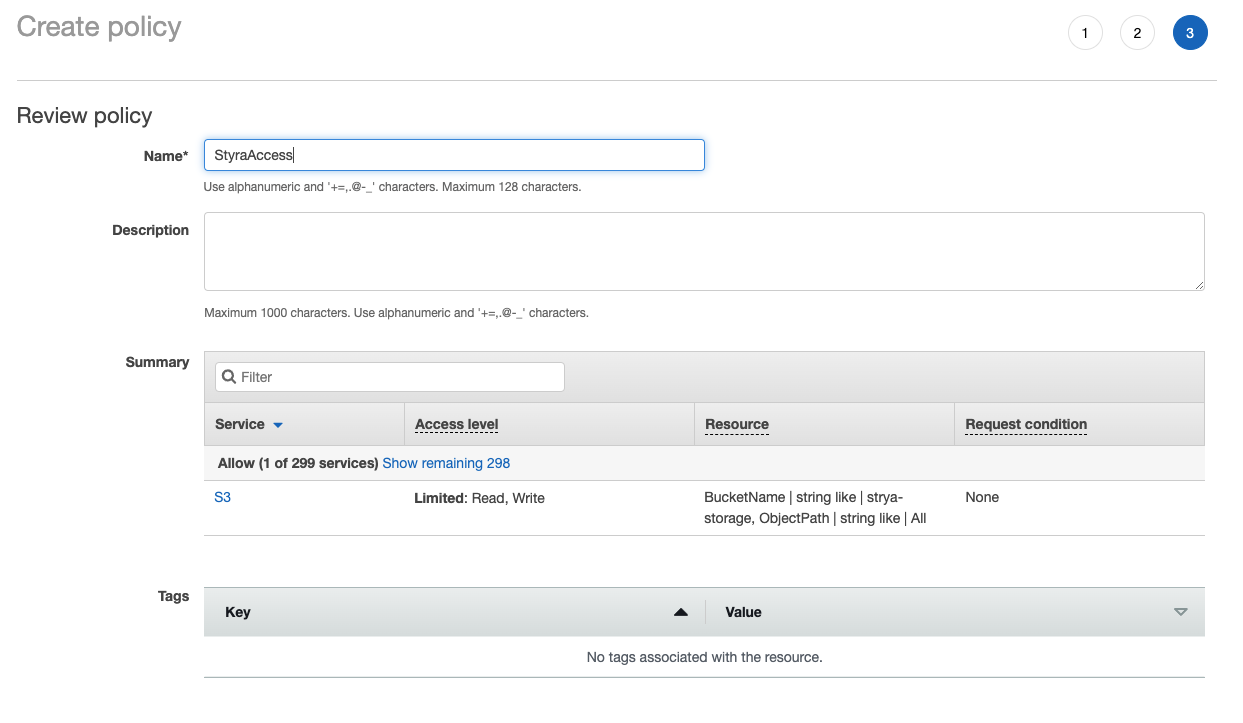 Figure 4 - IAM Review Policy
Figure 4 - IAM Review Policy
-
Attach the
StyraAccesspermissions to the user.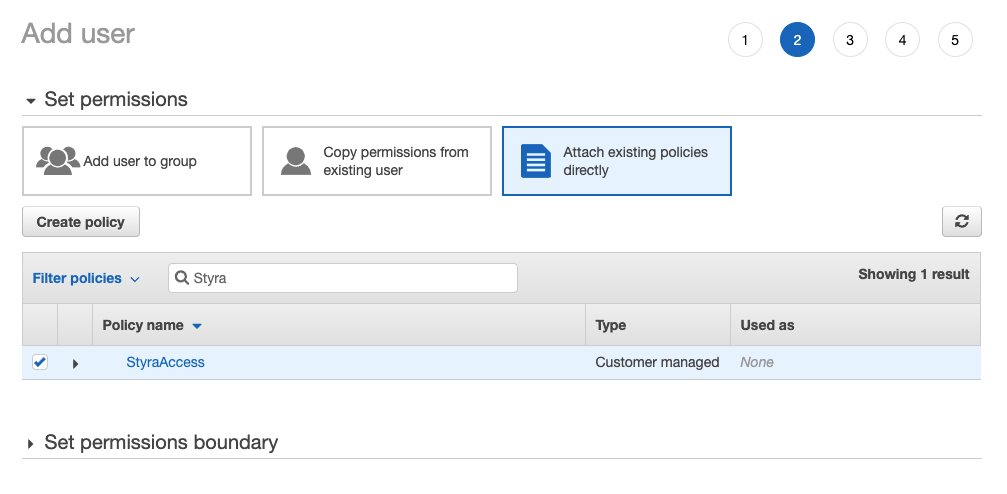 Figure 5 - IAM Permissions
Figure 5 - IAM Permissions
-
Save the created user's security credentials.
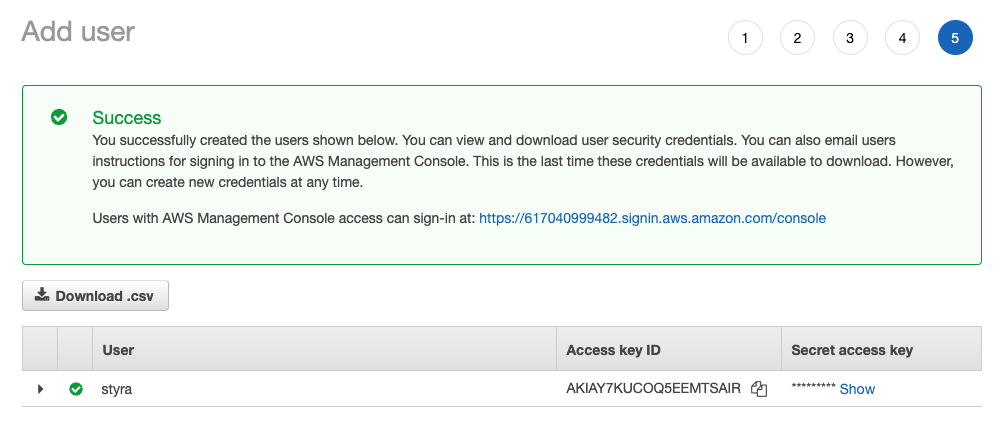 Figure 6 - IAM Keys
Figure 6 - IAM Keys
Save the user's Access key ID and Secret access key for later use when configuring DAS S3 components.
Use Amazon S3 Manager
Perform the following S3 storage actions:
-
Create an S3 bucket.
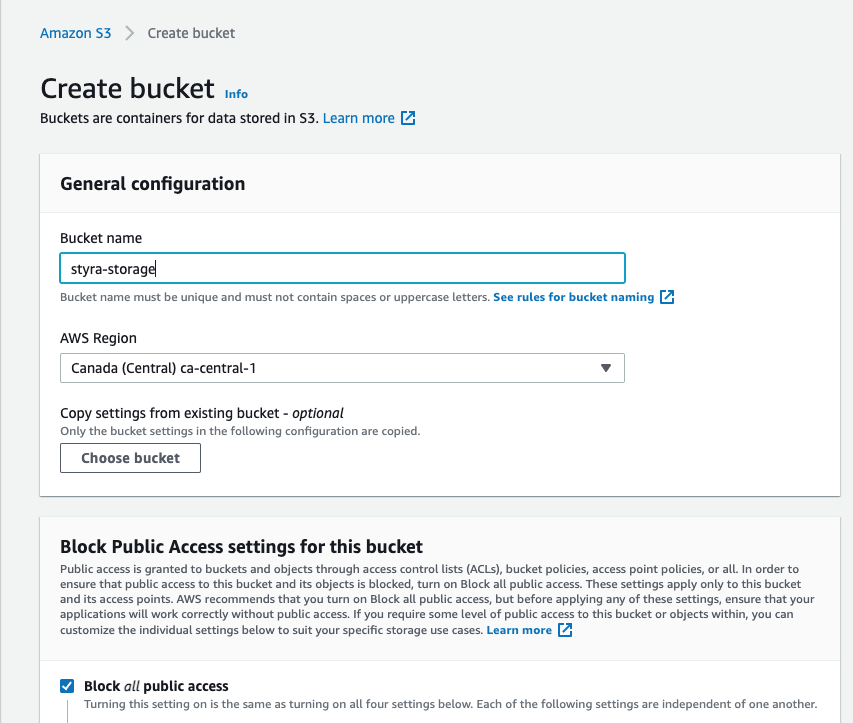 Figure 7 - Create a S3 Bucket
Figure 7 - Create a S3 Bucket
-
Create a bucket retention policy.
The Styra DAS decision and activity exporters may write large amounts of files to the S3 bucket, based on decision and user activity log volume. These files do not have a defined retention period by default. Add a bucket retention policy to archive, move, or delete files based on your organization's data retention policies.