Install the Kong Gateway Example Application
Configure kubectl to point to the cluster and namespace you want to use for the Kong Gateway example application.
To install Styra DAS on the Kong Gateway, copy and paste the installation commands from Systems > Settings > Install from the Kong Gateway System into your terminal. This will download and deploy the Styra Local Plane (SLP), OPA config, and the Kong Gateway configuration.
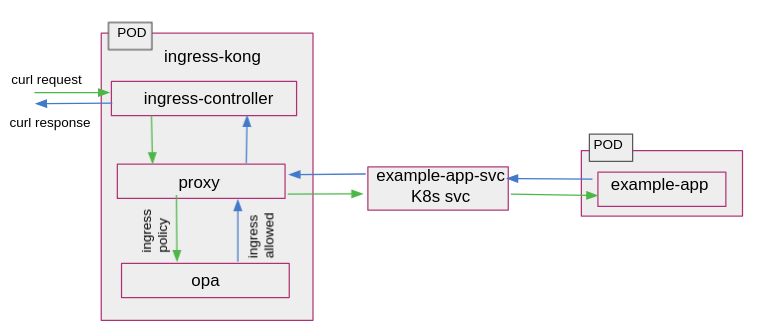
The Quick Start provides the link to install example application. It consists of the following components which should now be running in your cluster. All resources are suffixed by the SYSTEM ID to mark them as unique.
-
example-app: A simple HTTP web server that allows employees of a hypothetical organization to obtain salary details at the path/finance/salary. It also exposes a path/hr/dashboardthat is only accessible by employees who are part of HR. Functionally, it is a simple echo server that returns a HTTP 200 response with a plain or text body which contains a success or error message. -
example-ingress: An ingress resource which exposes HTTP route from outside the cluster to theexample-appservice within the cluster. The Kong plug-in for OPA is enabled by annotating the ingress resource withkonghq.com/plugins: kong-plugin-opa. -
slp: The Styra Local Plane (SLP) is a service that acts as an intermediary between the OPAs and Styra DAS. OPAs are configured to retrieve bundles from SLP rather than directly from Styra DAS. This increases availability as SLP fetches bundles from Styra DAS and persists them to disk. Policies are still available to new or restarted OPAs even if Styra DAS is unavailable.
When you run the Kong Gateway example application, the OPA sidecars accesses the policy from your Styra DAS tenant and starts enforcing the policy. This process takes a few minutes to complete.
 Kong Gateway Example Application
Kong Gateway Example ApplicationConfigure Kong Plug-in for HTTP
If you are using a Kong plug-in other than the Unix Domain Socket (UDS) based plug-in, The following files must be edited:
- Kong plug-in configuration file
- OPA sidecar values YAML configuration file
Kong Plug-in Configuration File
The Kong plug-in configuration file is added in the Kong Gateway Install section and can be used to configure the Unix Domain Socket (UDS) based plug-in. To configure the HTTP based plug-in, save the following KongPlugin configuration content into a new file (suggested name kong-plugin-http-config.yaml) and execute the kubectl -f apply kong-plugin-http-config.yaml command to apply the configuration.
---
apiVersion: configuration.konghq.com/v1
kind: KongPlugin
metadata:
name: kong-plugin-opa
config:
server:
host: localhost
port: 8181
policy:
decision: main/main
plugin: opa
OPA Sidecar Values YAML Configuration File
Save the sidecar deployment configuration into a new file (suggested name opa-sidecar-http-values.yaml), execute the helm upgrade kong-quickstart kong/kong -n kong -f opa-sidecar-http-values.yaml command to apply the configuration, and execute kubectl get pods -n kong -w command to watch for the Pod status to appear as Running status.
# -----------------------------------------------------------------------------
# Deployment parameters for HTTP configuration
# -----------------------------------------------------------------------------
deployment:
sidecarContainers:
- image: openpolicyagent/opa:latest
name: opa
volumeMounts:
- readOnly: true
mountPath: /config
name: opa-config
env:
- name: OPA_LOG_TIMESTAMP_FORMAT
value: "2006-01-02T15:04:05.999999999Z07:00"
args:
- "run"
- "--server"
- "--config-file=/config/conf.yaml"
- "--addr=http://localhost:8181"
ports:
- containerPort: 8181
userDefinedVolumes:
- name: opa-config
configMap:
name: opa-config
plugins:
configMaps:
- name: kong-plugin-opa
pluginName: opa