Update Terraform Infrastructure
With an enforced policy published for your Terraform system type, update the Terraform configuration and attempt a terraform apply to see if the change passes the Styra DAS Terraform policies.
Change the VPC CIDR Block
Let's make a change to the fake VPC resource in Terraform which violates the policy we created in the previous step.
Open the main.tf file from the example codebase for this tutorial in your code editor.
For the fakewebservices_vpc resource, change the cidr_block value to 10.0.0.0/16 and save your changes:
resource "fakewebservices_vpc" "primary_vpc" {
name = "Primary VPC"
cidr_block = "10.0.0.0/16"
}
Terraform Apply
In your terminal, run terraform apply to start a plan and apply for the VPC CIDR block change. Terraform will output the plan for the resource change in the terminal, after which the plan will be evaluated by Styra DAS via the run task integration.
After a few moments, you should see a Failed post-plan run task result with a policy evaluation summary.
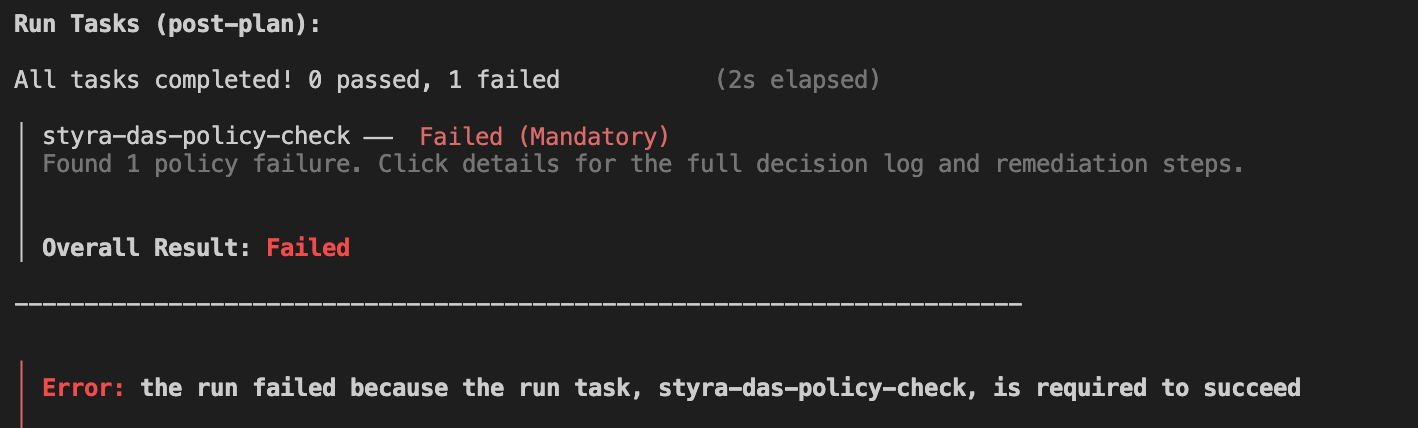 Figure 1 - Policy Failure
Figure 1 - Policy FailureYou can also see the policy evaluation summary message in Terraform Cloud by following the run link output by the Terraform CLI during the beginning of the run.
To receive Styra DAS policy evaluation feedback in the Terraform CLI during an apply command, you will need to use v1.1.9 or higher of the Terraform CLI. Using an older CLI version does not impact the policy evaluation in Styra DAS and Terraform Cloud.
Review the Styra DAS Decision
With the Terraform Cloud and Styra DAS integration, you can easily access the policy decision details from within Terraform Cloud runs.
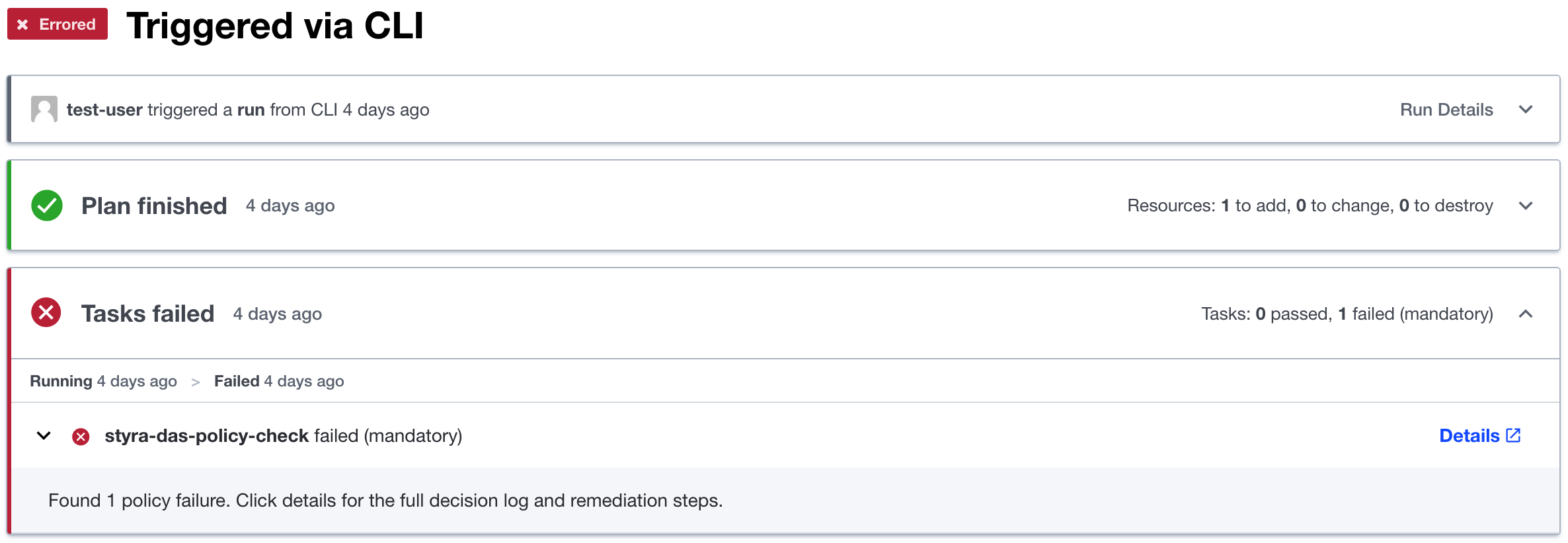 Figure 2 - Terraform Cloud Run
Figure 2 - Terraform Cloud RunClick the Details link on the Styra DAS policy check run task to be taken directly to the associated policy decision in Styra DAS. Here you'll see the decisions for your Terraform system, be able to view the input received from Terraform Cloud which led to the decision, and be able to replay the decision.
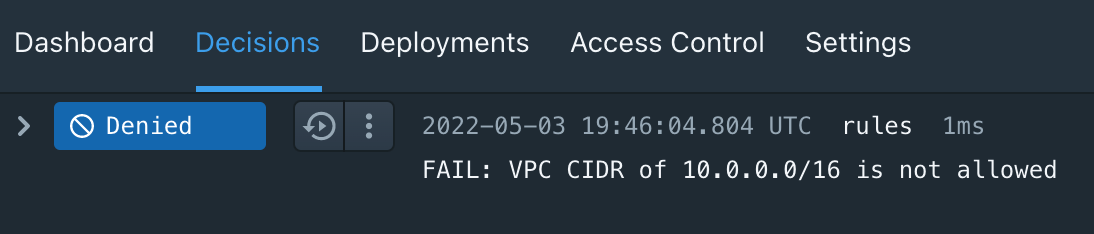 Figure 3 - Decision in Styra DAS
Figure 3 - Decision in Styra DAS