Preview
For this tutorial, you will define one Kubernetes audit and admission control rule that prevents users from creating conflicting inbound entry point ingresses for a system.
This specific rule is an example of a predefined built-in rule that implements a best practice. In this case, the rule helps you prevent an action. For example, a test application from receiving internet traffic from a production application.
This tutorial guides you through the following basic tasks:
- Add a system.
- Install an agent.
- Configure a built-in rule.
- Validate your configuration.
- Publish the rule in enforce and monitor modes.
This tutorial assumes that you are using the Open Policy Agent (OPA) to integrate with the Kubernetes admission control framework and that you access the Styra control plane using a cloud-based Styra tenant: <das-id>.styra.com for policy authoring, validation, and distribution.
In this scenario, OPA decides whether to allow or deny operations by evaluating your policies for Kubernetes resources each time the Kubernetes API is called.
The following figure provides an overview of the integration architecture when you use Styra for Kubernetes.
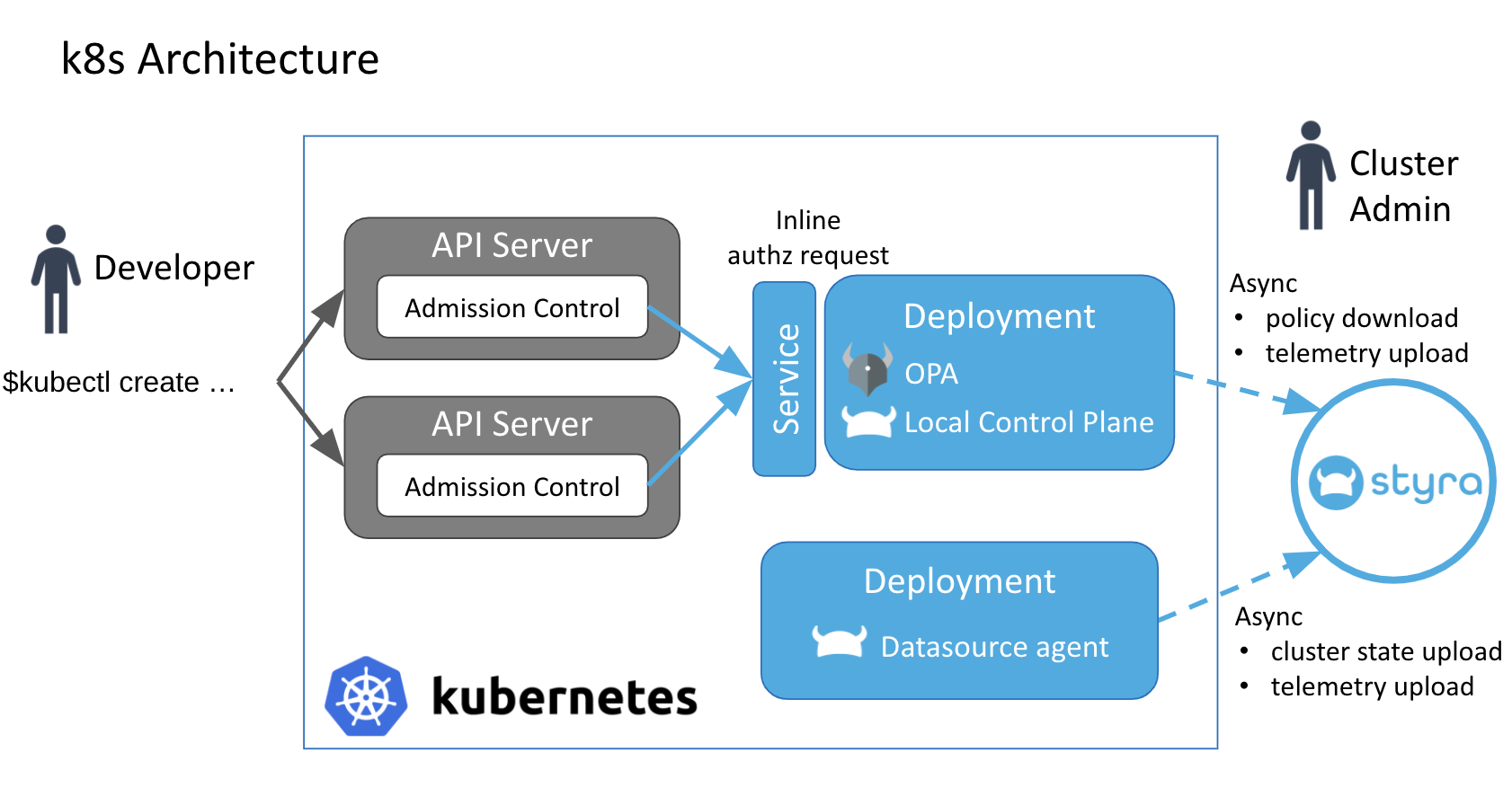 Figure 1 - Architecture of Styra for Kubernetes
Figure 1 - Architecture of Styra for Kubernetes